
While Nagios Logserver is a useful tool for system analysis and central log management, it is also a great tool to analyze network security. One can actually make use logserver to improve security by using it to dynamically block IP’s from malicious attackers. Assuming you are using OpenBSD as a gateway for incoming traffic which uses pf to block IP’s, to set up dynamic filtering you would do the following:
1. Install/Deploy logserver on a VM or normal server.
2. Install filebeat on any server with incoming traffic. In our case we have filebeat forwarding all /var/log/authlog logs to our logserver instance since this is where all the incoming traffic originates from.
a. Add the following to your /etc/filebeat/filebeat.yml (you really only need the /var/log/authlog line):

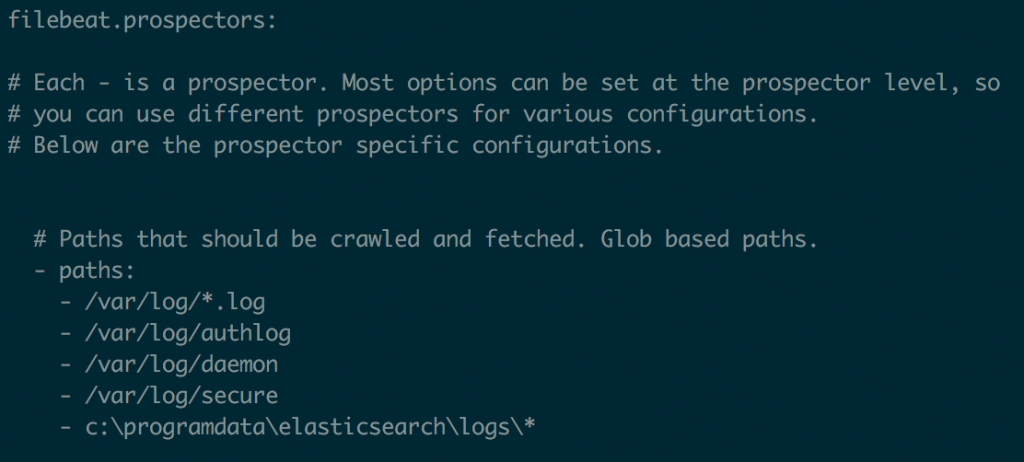

b. Make sure logserver is set up to receive the logs. To do this, go to the logserver web console then
and then go to Admin>Global Config. Create a new Input and add the following:
syslog {
type => 'syslog'
port => '5543'
}
5. Now we need to parse out all the malicious IPs from incoming login attempts. To do this we do the following:
a. Download the fetch_bad_ips.py script from https://github.com/Rex-Consulting/fetch-bad-ips to your logserver instance
b. Make sure it has execution permission
i. chmod 755 ./fetch_bad_ips.py
6. Now that we have a way to parse out malicious IPs from logs we need to add these IPs to a blacklist
a. Download ip_filter.sh from https://github.com/Rex-Consulting/fetch-bad-ips to your gateway server
b. Give it execution permission
i. chmod 755 ./ip_filter.sh
c. In order to have this script run periodically we need to run it through crontab
i. Run: crontab -e
ii. Add the following line: 0,10,20,30,40,50 * * * * /etc/cron.d/ip_filter.sh
iii. Save crontab (:w)
7. Lastly, to define your blacklist table do the following:
a. Append to the end of /etc/pf.conf:
table persist block on fxp0 from to any
b. Then restart the firewall:
pfctl -f /etc/pf.conf
6. To view the current blocked IPs, run the following command: pfctl -t testblacklist -T show
Note that other linux systems that use IP Tables can perform similar packet filtering. Contact us for details in our Contact Form.
© Copyright 2020 Rex Consulting, Inc. – All rights reserved